Friday, May 12, 2017 will forever be an omninous day for IT professionals across the the world. On that day, an unprecedented number of ransomware attacks swept across the globe, crippling Britain's National Health Service and affecting more than 200,000 people in over 150 countries.
According to Europol, those numbers will likely increase as many businesses may not have yet reported attacks. As the final tally increases and IT teams are repairing the damage, there are some key takeaways to help prevent your organization from being a victim of future ransomware attacks. The first thing to understand is how this particular piece of ransomware spread so fast and was so effective.
What is WannaCry?
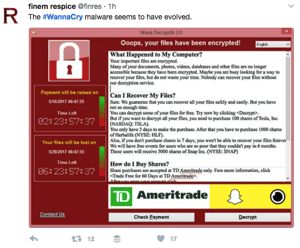
WannaCry is a type of malware called ransomware, which locks the data of a victim's computer and holds it unless a ransom is paid. Ransomware is typically distributed via email phishing attacks, whereby users open an attachment or click on a link that gives the ransomware an opening to breach the user's system. WannaCry took advantage of a hacking tool surreptitiously developed by the National Security Agency to target a specific vulnerability in Windows operating systems that made it more viral than previous ransomware attacks. The exploit that WannaCry used is called EternalBlue, which targeted a security loophole in Windows operating systems that allows malicious code (in this case ransomware) to spread through existing file sharing structures without permission from users. That meant from one remote computer, an entire company can be shut down. And if files are shared with other companies, WannaCry could spread through those files as well.
Lesson #1: Keep Your Systems Updated
The loophole the EternalBlue exploit took advantage was addressed in a security update by Windows before Friday's attacks. Yet countless of victims were affected because they were using older Windows systems that were not part of any automatic update. The problem was so severe that Windows broke from tradition and offered a free security patch for older systems like Windows XP. Ironically, it's the larger organizations that are often at the most risk, because updating hundreds of PC's can have higher costs associated than doing a custom patch to address any security issues. This gets even trickier after years of customizations build up. The result is thousands of companies still running Windows 7 and Internet Explorer 8, leaving themselves open to attacks like WannaCry. Future considerations of software updates (versus patches) will now have to take into consideration the risk mitigation of another large scale attack. This is especially true since attacks like WannaCry are not over. A new variant has already popped up called Uiwix, which circumvents the "kill switch" that helped to slow down WannaCry's spread. If updating your system isn't an option, then the vehicle the exploit uses can be disabled.
Lesson #2: Train your staff
Ransomware is becoming a go-to choice for hackers because it's an easier way to extract money from a hack than trying to sell PHI on the black market. It also relies heavily on the weakest part of any cybersecurity plan - people. One of the most vital parts of any plan is to train your staff on how to avoid falling for phishing and spam emails that contain malware. This includes recognizing what is a suspicious email and never downloading attachments or clicking on links in those emails. Having a good spam filter will help reduce some of the risks, but a solid training plan will further reduce potential breaches. One of the most important parts of any plan is to train staff on what to do if they notice anything suspicious. It's not enough to avoid the email, but be sure there's a system to report emails and any breaches which limits the stigma of falling for a phishing email. The worst thing that could happen is a staff member falls for the phishing attack and waits to take action because they are worried about looking foolish.
Lesson #3: Assume you'll be affected
Always hope for the best and plan for the worst. Assuming that you will eventually be hit by ransomware will help you put in place the right procedures to mitigate risks and limit any damage. Sticking your head in the sand and hoping for the best should never be an option. Here are a few steps you should consider:- Backup your data offsite, whether that's in the cloud or servers at other locations.
- Turn off file sharing by default and only sync when necessary (This may be easier said than done).
- Be sure users only have enough access as needed to do their jobs.
- Turn off macros in Microsoft Office (again, easier said than done).
- Remove often exploited plugins from browsers such as Adobe Flash and Java.
- System admins should work daily in a restricted role unless admin access is needed.
- Consider an ad blocker on your browser to avoid malicious ads.
Can a future WannaCry be prevented?
This is the multi-million dollar question the entire cybersecurity community is asking themselves. And the answer is probably not. But that doesn't mean that it's doom and gloom. While other attacks can and will happen, the silver lining is there are lots of things that can be done to drastically limit the impact of a ransomware attack. WannaCry showed the world that it's never too early to begin maintaining and executing a cybersecurity plan.
