When implemented collectively, HIPAA's administrative, technical, and physical safeguards work together to ensure the protection and security of patient information. An in-depth understanding of each allows healthcare organizations to understand their responsibilities in protecting patient data.
Understanding technical safeguards
Technical safeguards are the security measures that protect electronic protected health information (ePHI) and control access to it. These act as a central part of HIPAA's Security Rule because they help to protect ePHI from unauthorized access, alteration, or destruction.
Implementing technical safeguards
- Firewalls: Set up firewalls to control and monitor incoming and outgoing network traffic. Firewalls act as a barrier between internal networks and the external Internet, allowing organizations to define and enforce rules for network communication.
- Intrusion detection and prevention systems (IDS/IPS): Deploy IDS/IPS tools to detect and prevent unauthorized access or malicious activities within the network.
- Malware protection: Implement robust antivirus and anti-malware software to detect and remove malicious software from systems.
- Patch management: Keep all software and operating systems up to date with the latest patches and security updates.
- Secure configuration: Configure systems and devices securely, following best practices and recommended guidelines.
- Logging and monitoring: Implement logging mechanisms to record and monitor system events, network activities, and user actions.
Benefits and Impact of technical safeguards
Technical safeguards help mitigate risks associated with cyber threats, hacking attempts, malware infections, and other security incidents. By deploying firewalls, intrusion detection systems, and malware protection, which minimizes potential damage and financial losses the organization may experience.
Implementing technical safeguards can give organizations a competitive edge in an age where data breaches and security incidents are prevalent. Demonstrating a commitment to security and privacy can differentiate a company from its competitors and attract security-conscious customers and business partners.
Challenges with technical safeguards
Implementing technical safeguards requires a deep understanding of various technologies, security protocols, and best practices. It can be challenging for organizations with limited technical expertise or resources to navigate and implement security measures effectively.
Organizations also often rely on third-party vendors, cloud service providers, or partners to deliver certain IT services or store data. Ensuring these entities have adequate security measures in place and align with the organization's security standards can be challenging, as the organization has limited control over external systems.
Related: What are administrative, physical, and technical safeguards?
Best practices to navigate the technical safeguards
- Conduct a thorough risk assessment: Conduct a comprehensive risk assessment to identify potential vulnerabilities and risks within your organization's systems and infrastructure. This assessment will serve as a foundation for implementing appropriate technical safeguards.
- Develop and enforce strong access controls: Implement a robust access control system to ensure that only authorized individuals can access sensitive patient information. This includes unique user IDs, strong passwords, multi-factor authentication, and regular access reviews.
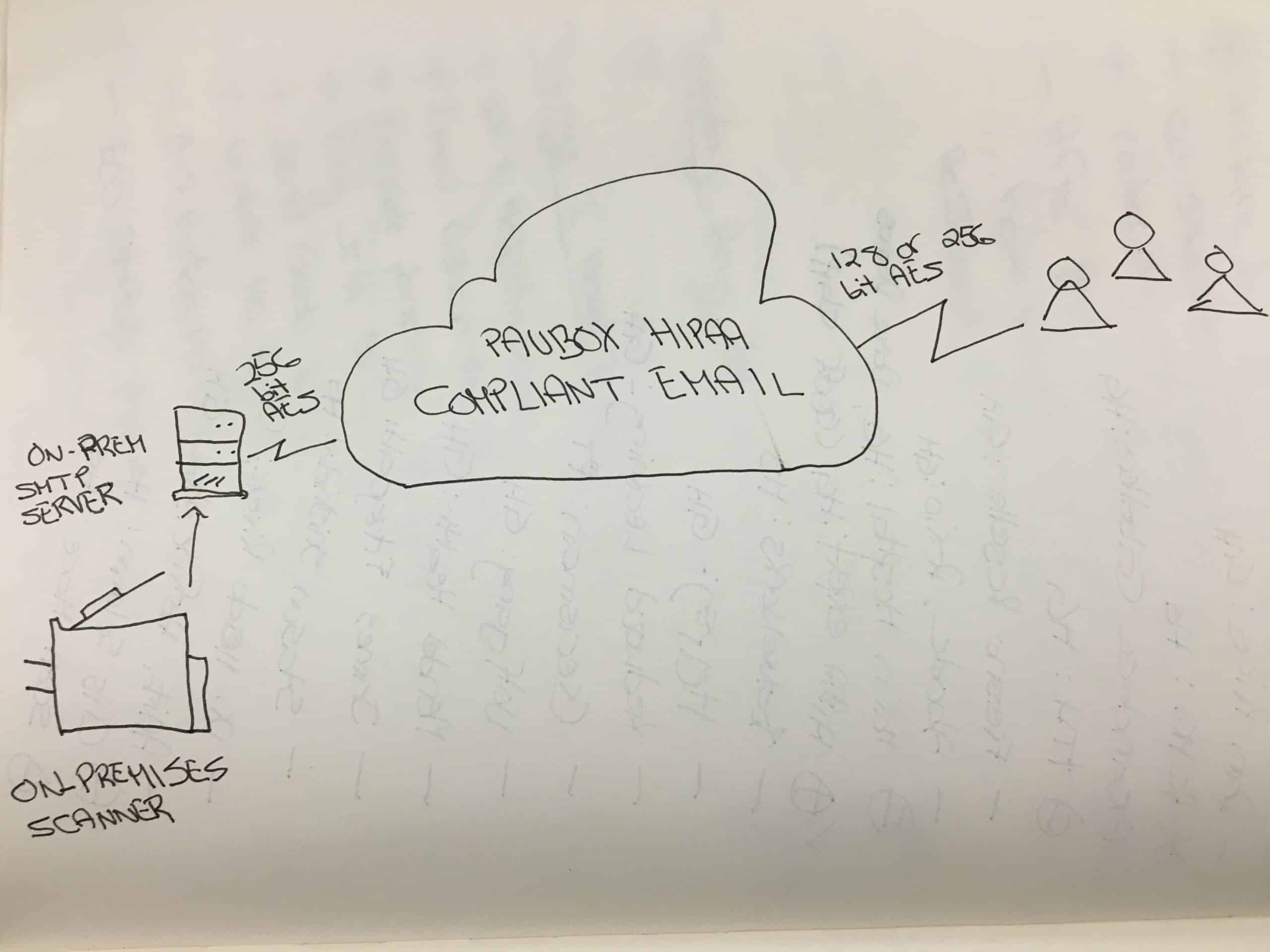
- Encrypt sensitive data: Implement encryption mechanisms to protect sensitive data both at rest and in transit, for example, by using encrypted, HIPAA compliant email. Utilize industry-standard encryption algorithms and protocols to secure electronic health records (EHRs), backups, and communication channels.
- Implement firewalls and intrusion detection/prevention systems: Install and configure firewalls to control incoming and outgoing network traffic. Additionally, deploy intrusion detection and prevention systems (IDPS) to monitor and respond to potential cyber threats.
- Regularly update and patch systems: Stay up to date with the latest security patches and software updates provided by your vendors. Regularly patching and updating your systems can help mitigate vulnerabilities and protect against known security flaws.
- Utilize secure email and file transfer protocols: Implement secure email and file transfer protocols (such as S/MIME, PGP, or encrypted file transfer protocols) to ensure the confidentiality and integrity of sensitive information shared through electronic communication. Alternatively, make use of HIPAA compliant email services to encrypt email.
- Establish data backup and recovery mechanisms: Develop and implement a robust data backup strategy to ensure that critical patient information is regularly backed up and can be quickly restored in case of a system failure, data breach, or disaster.
- Implement intrusion prevention mechanisms: Deploy intrusion prevention mechanisms, such as intrusion detection systems (IDS), intrusion prevention systems (IPS), and security information and event management (SIEM) tools, to proactively monitor network traffic, detect potential threats, and respond promptly.
Go deeper:
Subscribe to Paubox Weekly
Every Friday we'll bring you the most important news from Paubox. Our aim is to make you smarter, faster.