
HIPAA compliance in email communications requires encryption like TLS 1.2 or 1.3 and implementing secure policies and procedures.
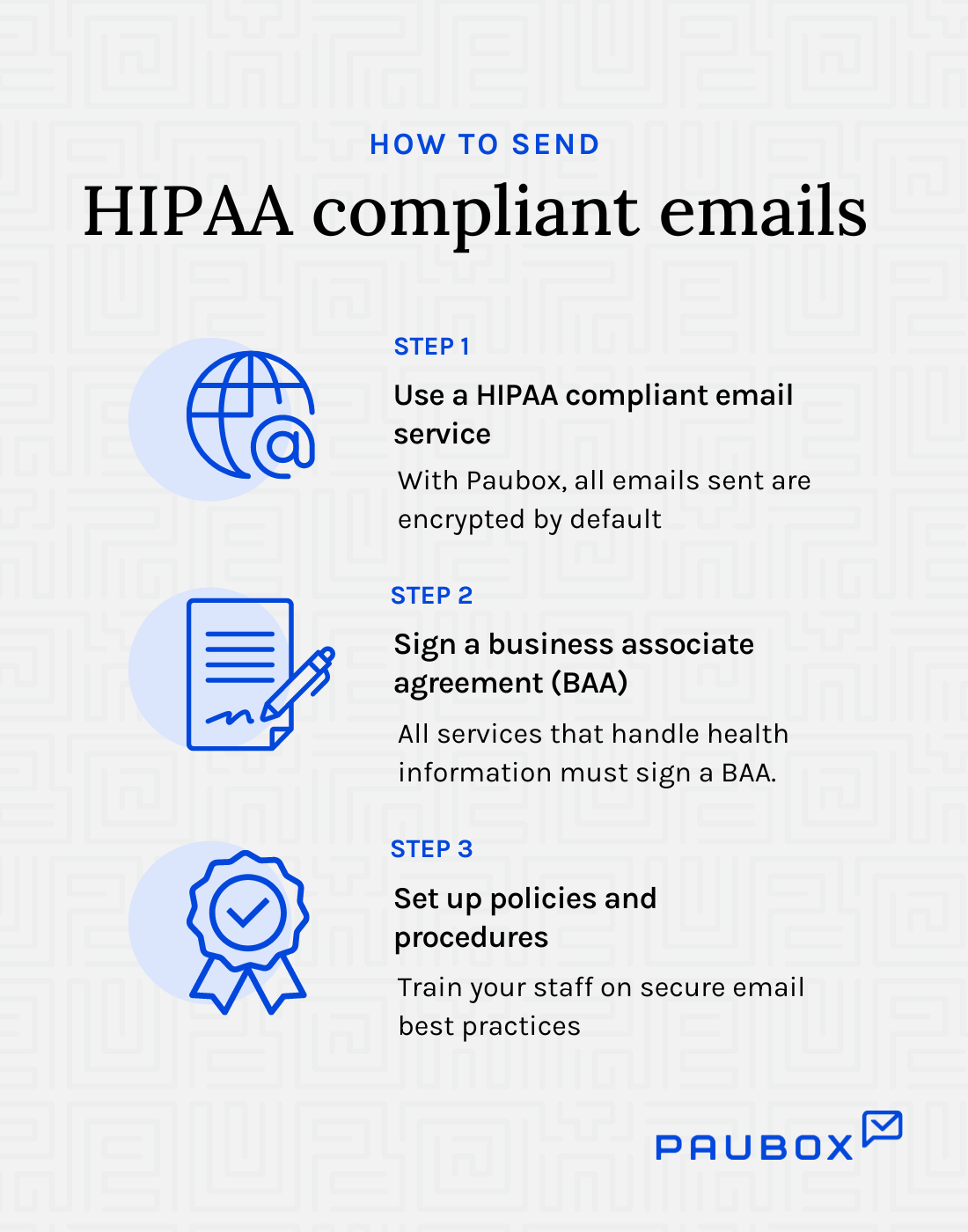
How to make your email HIPAA compliant
Encryption
Encryption protects protected health information (PHI) from unauthorized access during transmission. By converting the data into a secure format, encryption ensures that even if the email is intercepted, the contents remain unreadable to anyone without the proper decryption key. TLS 1.2 or 1.3 is the form of encryption recommended by the NIST due to its strong encryption algorithms and improved handshake processes.
Practically speaking, use a HIPAA compliant email service, like Paubox, to comply with HIPAA email requirements. Paubox Email Suite works with Google Workspace or Microsoft 365 and encrypts all outgoing emails automatically, with no extra steps.
BAA
A business associate agreement (BAA) is a contract between a HIPAA-covered entity (hospitals, practices, etc.) and a third party, known as a business associate, who handles PHI on behalf of the covered entity. A BAA should be in place with email providers because it legally binds the provider to comply with HIPAA regarding the protection of PHI. The BAA outlines the email provider's responsibilities for safeguarding PHI, ensuring secure transmission and storage, and reporting any data breaches.
The standard components of a BAA:
- Defines permissible uses and disclosures of PHI
- Requires the business associate to implement safeguards for PHI
- Mandates the reporting of data breaches or unauthorized disclosures
- Specifies the return or destruction of PHI upon contract termination
- Outlines the procedures for auditing and monitoring compliance
- Includes clauses on subcontractor compliance with HIPAA rules
Policies
According to the HHS, "Given that the health care marketplace is diverse, the Security Rule is designed to be flexible and scalable so a covered entity can implement policies, procedures, and technologies that are appropriate for the entity's particular size, organizational structure, and risks to consumers' e PHI."
HIPAA compliant policies and procedures are the documented rules and guidelines that healthcare organizations follow to protect patient information and ensure privacy and security. These policies and procedures are necessary because they cover a wide range of internal matters specific to the organization that demonstrate the organization's commitment to HIPAA compliance.
Retention
Retention policies are guidelines that specify how long a healthcare organization must keep PHI. While not a requirement under HIPAA (as retention legislation is generally left to state law), the Privacy Rule does require "...that covered entities apply appropriate administrative, technical, and physical safeguards to protect the privacy of medical records and other PHI for whatever period such information is maintained by a covered entity, including through disposal."
The purpose of retaining PHI is multifaceted: it ensures that patient records are readily available for ongoing treatment, fulfills legal and regulatory requirements, supports audits and investigations, and maintains continuity of care. These policies ensure that PHI, especially that which is held in email, is securely stored for the required period and properly disposed of when no longer needed.
There are no HIPAA medical records retention requirements, though requirements do exist documentation like:
- Policies and procedures
- Complaints
- Dispositions
- Security Rule assessments
- Breach notification records
Organizations should also retain documents related to incident responses and other actions to ensure HIPAA compliance. Health practitioners must maintain these records for six years from their creation date or the date they were last in effect. Keeping records beyond the minimum required period is often worthwhile to meet potential legal, operational, or clinical issues.
Authorization, consent, and the NPP
Authorization under the HIPAA Privacy Rule is a detailed, written permission that a patient gives to a healthcare provider or organization to use or disclose their PHI for specific purposes not otherwise covered by the rule. General consent covers routine uses and disclosures of PHI for treatment, payment, and healthcare operations.
Consent allows healthcare providers to use and disclose PHI for treatment, payment, and healthcare operations, which includes standard communication like email. The Notice of Privacy Practices (NPP) outlines these uses, and patients give their general consent by acknowledging the NPP.
Digital consent methods sent through email, like Paubox forms with digital signatures, remain the best way to sign NPPs and patient authorizations because they provide a secure, efficient, and verifiable way to obtain and document patient permissions.
Alternative communication
Alternative methods of communication are necessary alongside HIPAA compliant email because there are situations where email may not be suitable. For instance, some patients might not have reliable access to email, may prefer more immediate forms of communication, or may require more secure methods for highly sensitive information. Alternative methods, such as secure messaging apps, phone calls, or postal mail, ensure that all patients receive health information in a timely and accessible manner.
What HIPAA regulations actually say about email
The Security Rule sets up the guidelines to protect various areas in healthcare organizations to ensure that PHI remains safe. This guidance is divided into the Administrative, Physical, and Technical Safeguards, covering each area of potential unauthorized access or breach.
Administrative safeguards include implementing detailed policies and procedures that govern the use of email for PHI. The following statement is a notable portion of the safeguard, "A covered entity must reasonably safeguard protected health information from any intentional or unintentional use or disclosure that is in violation of the standards…"
These policies must cover how PHI is handled, who is authorized to access it, and the protocols for secure communication. Healthcare organizations must also designate a privacy official responsible for developing and implementing these policies. Additionally, all staff members must be trained on these policies and procedures to ensure they understand how to handle PHI securely and in compliance with HIPAA regulations.
Technical safeguards focus on the technologies used to protect PHI during email transmission and storage. According to the HHS Security Series, the purpose of the technical safeguards is, "Implementation of the Technical Safeguards standards represent good business practices for technology and associated technical policies and procedures within a covered entity."
Secure access controls, such as strong passwords and two-factor authentication, must be implemented to restrict access to email accounts that handle PHI. Organizations must also maintain audit controls, which involve tracking and logging email activities to monitor for any unauthorized access or breaches. These logs help identify and address security incidents promptly.
Physical safeguards pertain to the physical security of the devices and environments used to access and send emails containing PHI. An interesting portion of Section 164.310 is its specification of disposal requirements, "Disposal (Required). Implement policies and procedures to address the final disposition of electronic protected health information, and/or the hardware or electronic media on which it is stored."
Physical safeguards also include measures such as secure disposal of devices, regular maintenance of security software, and using secure, private networks for accessing email.
Best practices
Encrypting every email by default is necessary to ensure the security of PHI during transmission. When an email is encrypted, its contents are transformed into a coded format that only authorized recipients with the correct decryption key can read. By encrypting all emails, healthcare organizations protect sensitive information from potential breaches. Default encryption also mitigates the risk of human error, as users do not need to decide which emails require encryption.
Using HIPAA compliant email software is the best option for implementing this practice effectively. This software is designed to meet HIPAA's security requirements, incorporating encryption protocols and secure access controls. It also includes features like automatic encryption, secure user authentication, and audit trails that track email activity, providing a comprehensive security solution. HIPAA compliant email software simplifies compliance efforts, reducing the administrative burden on healthcare organizations.

HIPAA compliant checklist
1. Encryption
- Encrypt all emails containing PHI during transmission.
- Use TLS for email encryption.
2. Secure storage
- Store emails containing PHI securely with encryption.
- Use secure servers and encrypted storage solutions.
3. Policies
- Develop and implement detailed policies and procedures for email communication.
- Include protocols for sending, receiving, and storing emails with PHI.
4. Training
- Train all workforce members on HIPAA compliant email practices.
- Conduct regular training sessions and refreshers on updated policies.
5. Minimum Necessary Principle
- Ensure emails contain only the minimum necessary PHI required for the intended purpose.
- Limit access to PHI based on job roles and responsibilities.
6. Breach policies
- Develop and implement an incident response plan for potential breaches involving email communications.
- Include procedures for reporting, mitigating, and documenting breaches.
7. Access control
- Implement strong access controls, such as unique user IDs, secure passwords, and multi-factor authentication.
- Restrict access to email accounts handling PHI to authorized personnel only.
8. BAAs
- Establish BAAs with email service providers to ensure they comply with HIPAA regulations.
- Ensure providers understand their responsibilities in protecting PHI.
9. NPP
- Inform patients through the NPP about the use of email for communication.
- Obtain patient consent for email communication of PHI.
10. Physical safeguards
- Secure devices are used to access and send emails containing PHI.
- Implement measures to protect workstations and mobile devices from unauthorized access.
11. Audit controls
- Maintain audit trails to track email activity, including access, sending, and receiving of emails containing PHI.
12. Ongoing monitoring and updates
- Regularly review and update email policies and security measures.
- Stay informed about new threats and changes in HIPAA regulations.
13. Documentation
- Document all policies, procedures, and training efforts.
- Keep records of all email-related activities involving PHI for compliance verification.
14. Patient communication preferences
- Respect and document patient preferences for communication methods.
- Ensure alternative communication methods are available for those who do not prefer email.
Download the HIPAA compliant email checklist 2024: What you need to know
In the news
Major healthcare organizations impacted by data breach
Recent email security breaches at Children's Health Care in Minnesota and the Los Angeles County Department of Mental Health have exposed the PHI of thousands of patients. At Children's Health Care, unauthorized access to two employee email accounts between February 29 and March 25, 2024, compromised sensitive data related to the hospital's surgical services, affecting 7,260 patients.
The hospital promptly reported the breach to the Office for Civil Rights and is enhancing its cybersecurity measures. Meanwhile, the Los Angeles County Department of Mental Health experienced a phishing attack on March 20, 2024, leading to the exposure of PHI for 1,598 patients, including Social Security numbers. The department has since updated its security policies and implemented additional safeguards.
Winter Haven Hospital suffers data breach due to employee error
The data breach at BayCare's Winter Haven Hospital, caused by an employee mistakenly sending an email with an attached file containing other patients' PHI, exemplifies a lack of compliance with specific requirements of the HIPAA Security Rule.
This incident indicates a failure to implement adequate administrative safeguards, which include policies and procedures to prevent, detect, contain, and correct security violations. Specifically, the lack of proper training and protocols to avoid such errors indicates noncompliance with the Security Rule's requirements for workforce training and secure handling of PHI.
Google implements measures to prevent spoofing
Google has enhanced its phishing defenses by automatically blocking emails from bulk senders who fail to meet stricter spam thresholds and authentication requirements. These new measures, implemented in April 2024, require senders to authenticate their messages using SPF, DKIM, and DMARC, avoid sending unsolicited emails, provide easy unsubscribe options, and maintain low spam rates.
Noncompliant emails may be rejected or sent to spam folders. Google's AI defenses aim to block nearly all unwanted emails, improving email security for users. This initiative ensures the authenticity of emails, protecting users' sensitive information and enhancing overall online security by preventing spoofing and phishing attacks.
Case studies
North Mississippi Health Service
North Mississippi Health Service, a hospital system with locations across Mississippi and Alabama, faced the challenge of engaging the community while ensuring HIPAA compliance in their communications. To address this, they adopted Paubox Marketing for sending personalized, secure newsletters. Robin McKinney, NMHS' Digital Marketing Strategist, mentioned the need for email to reach people directly instead of relying solely on social media or the hospital's website.
With Paubox, NMHS can segment its audience and send relevant health information without risking PHI exposure, thanks to built-in encryption and compliance features. The intuitive interface and analytics of Paubox make it easy for the team to use and evaluate their email campaigns. The initial results were impressive, with the first newsletter driving patient engagement and subsequent newsletters reaching around 86,700 individuals with high open rates.
Cost Plus Drugs
Mark Cuban's Cost Plus Drugs has transformed the pharmaceutical industry by reducing medication prices through a transparent pricing model and eliminating middlemen. To maintain secure and HIPAA compliant communication, Cost Plus Drugs relies on Paubox for email encryption, marketing, and forms. Initially, the company used Outlook's encryption, which required manual selection and portal access for recipients, creating a cumbersome experience. Seeking a more user-friendly solution, they turned to Paubox.
Paubox Marketing allows the company to send automatically encrypted marketing emails containing PHI without requiring recipients to use portals, resulting in higher open rates and more effective campaigns. Paubox Email Suite ensures that all emails are encrypted by default, simplifying secure communication for both senders and recipients. This seamless encryption process has improved user experience and saved time, enhancing the company's operational efficiency.
Cost Plus Drugs also uses Paubox Forms to securely collect customer information, assisting their support team. Since adopting Paubox, the company has experienced uninterrupted, secure communications, thanks to the smooth transition facilitated by Paubox's support team.
The Caregiver Foundation
The Caregiver Foundation, a Hawaii-based non-profit organization, supports seniors, disabled adults, and their caregivers by providing practical and emotional assistance. To securely handle the exchange of sensitive patient details and PHI via email, they adopted Paubox Email Suite Plus in June 2015. This solution allows The Caregiver Foundation to effortlessly send HIPAA compliant, encrypted emails.
Paubox Email Suite Plus enables users to send emails as usual without requiring plug-ins or additional steps, and recipients can open secure emails without email portals or extra passwords. This seamless process ensures that PHI is securely transmitted to third-party agencies and field staff. Additionally, the solution offers robust protection against phishing, malware, and email bomb attacks, preventing email breaches.
Founder and Executive Director Gary A. Powell discussed the importance of these features, stating that Paubox's technology and HITRUST CSF certification were a part of their decision. The Paubox team assisted with migrating inbox accounts and familiarizing staff with the encryption process.
See also: Top 12 HIPAA compliant email services
FAQs
Does HIPAA apply to email?
Yes, HIPAA applies to email when it involves the transmission of PHI.
Can a HIPAA form be emailed?
Yes, a HIPAA form can be emailed if it is sent using secure, encrypted methods that comply with HIPAA.
What is an example of a HIPAA violation email?
An example of a HIPAA violation email is an unencrypted email containing PHI sent to the wrong recipient.
How do you know if an email is HIPAA compliant?
An email is HIPAA compliant if encrypted, sent using secure methods, and follows all administrative, technical, and physical safeguards required by HIPAA.
Subscribe to Paubox Weekly
Every Friday we'll bring you the most important news from Paubox. Our aim is to make you smarter, faster.




