Having been in the email security business for nearly 14 years, I've noticed a central theme around 99% of all junk mail I come across: It's about money.
For example, we've previously covered that healthcare data is much more valuable to hackers on the black market. Little surprise then, that phishing, spam, and malware attacks spike during the Christmas holiday season. More people are out shopping and getting email alerts about special deals and Black Friday sales.
Make no mistake: The bad guys cloak themselves in this buying environment. This post covers some of the more complex attacks on email security we've seen this Christmas season.
READ MORE: Build A Rock-Solid Email Security Strategy
Method A: Cloaking Website Origin
A reliable method of detecting a phishing or malware attack is to inspect any URL listed in an email message. If a URL listed in an email points to a suspicious or hacked website, advanced email security products like Paubox can detect and take action on that message.
For example, we implement Google's Safe Browsing API to help with URL detection. But what if you could cloak the origin of your phishing/malware website?
In the early days of phishing and malware attacks (circa 2004-06), the IP addresses used to setup these fake sites were fairly straightforward to detect. The bad guys would look for a web hosting company that had lax security policies and/or was located in a country that looked the other way. They'd sign up as a customer and then go to work building a phishing/malware website.
In today's world however, their methods have grown more complex. The bad guys now cloak the true origin of their phishing and malware websites.
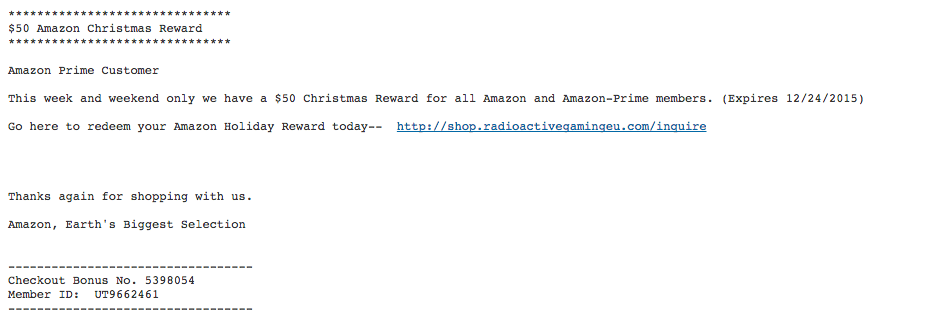
Let's take a look at an example:
The increasing complexity in email security
In the above phishing attack, the recipient is offered a $50 Amazon Christmas Reward by clicking on http://shop.radioactivegamingeu.com/inquire
To most humans, that's obviously *not* a website affiliated with Amazon. To a computer algorithm however, the best way to determine that is to see who the website belongs to. If we take a look, we see that it resolves to two IP addresses: 104.31.65.24 104.31.64.24
Ok great, who owns those IP addresses?
As it turns out, they belong to CloudFlare. CloudFlare is a legit U.S. company that provides a content delivery network and distributed domain name server services. In other words, they sit between the visitor and the CloudFlare user's hosting provider, acting as a reverse proxy for websites.
In this case however, they are inappropriately used to cloak the true identity of the phishing/malware site. CloudFlare has lots of useful abilities and is well regarded in the industry. Shucks, if an algorithm blocks or bans CloudFlare IP addresses, that's going to cause a lot of false positives (i.e. problems).
Method B: Opportunistic Email Server Rotation
Another time-tested detection method involves looking at the host or IP address that sends an email. If an email comes from an unreliable or compromised source, proactive action can be taken. There are many services that compile realtime lists of bad hosts on the Internet.
Spamhaus for example, is one of the more well-known providers. What if you could figure out how to constantly rotate the origin of your email IP address? A key component of tracking spam operators and sources is to first get actionable data. In other words, you should collect proof before committing an IP address or host to a realtime blacklist.
Therein lies a window of opportunity: The time a phishing/malware email is sent and the time it takes for that sending IP address to get blacklisted. Even if that window is hypothetically only four hours, the bad guys can pump out a ton of junk mail in that time.
Here's where the automation of evil intent comes in. In our example above, if it takes four hours to get detected, the bad guys opportunistically change the sending IP address of the same phishing/malware attack every 3 hours. In a nutshell, the same scam can be sent out to millions of people in a single day while staying just a small step ahead of the good guys. Yikes.
Conclusion: Email Security is a Vigilant Endeavor
As 2015 comes to a close, we can think of the Internet as an unruly teenager. It's grown up a lot since the first Dot-Com Boom. It's faster, friendlier and available to billions of people. Despite those gains however, there's clearly more maturation in order. An obvious example is email.
In today's environment, it can be abused, forged and intercepted by third parties. With the available tools and standards, one of the better approaches seems to be hybrid vigilance. A noteworthy example would be the resolution behind the aforementioned phishing attack via website cloaking and CloudFlare. CloudFlare CEO Matthew Prince quickly replied to my tweet on the matter and gave direction on how to submit an abuse report.
Going into 2016, I forecast email to remain at the forefront of both business use and opportunities for improvement.
We at Paubox endeavor to provide business leadership in this regard.
Subscribe to Paubox Weekly
Every Friday we bring you the most important news from Paubox. Our aim is to make you smarter, faster.

 Hoala Greevy
Hoala Greevy