According to Mimecast, “Sender Policy Framework (SPF) is an email authentication method that helps to identify the mail servers that are allowed to send email for a given domain. By using SPF, ISPs can identify email from spoofers, scammers and phishers as they try to send malicious email from a domain that belongs to a company or brand.”
How does SPF work?
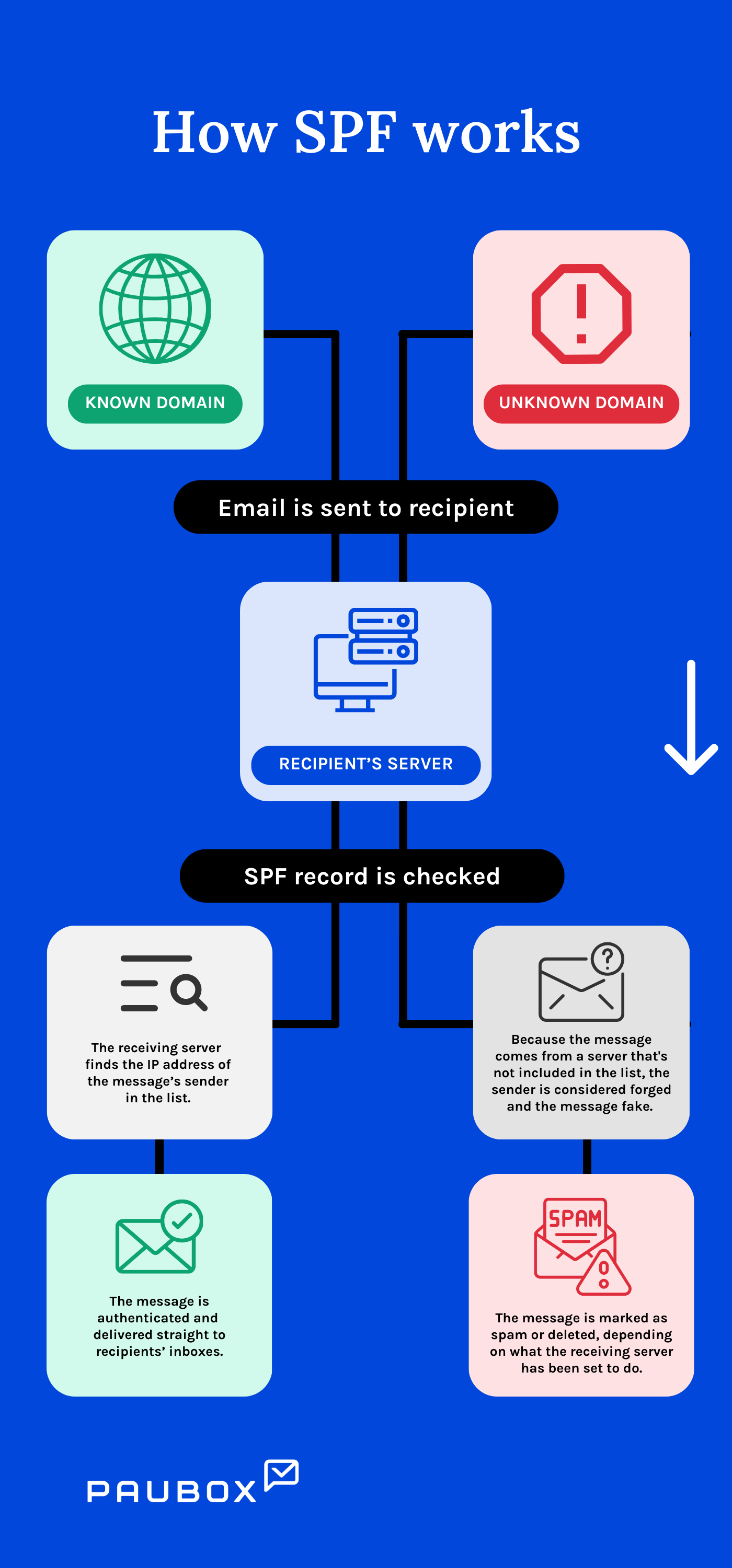
Generally, SPF establishes a policy called an SPF record that outlines which mail servers are authorized to send email from a domain. When an inbound server receives incoming mail, it references the rules for the bounce domain in the DNS and compares the IP address of the incoming mail to the authorized addresses defined in the SPF record. The receiving server then uses SPF record rules to determine if the incoming message will be accepted, rejected, or flagged.
Read also: What is an SPF record and why you need it
Importance of SPF
A sender policy framework provides users with an additional layer of cybersecurity. It enables domain owners to create a list of approved inbound domains to minimize the risk of receiving malicious emails. It helps other servers verify your domain's legitimacy.
Without an SPF record, malicious actors can spoof your domain and networks, harm your reputation, and carry out cyberattacks that result in financial loss. Furthermore, if you don’t have an SPF, servers that receive your emails may flag or reject them because they can't determine the authenticity of your domain.
Go deeper:
Cyberattacks on the healthcare sector
The limits of SPF
While the sender policy framework offers some protection against spam and spoofing, it is not a complete email security solution. A forwarded email will evade an SPF test, and the SPF protocol can only spot email that spoofs the "from" address – the address that's visible to users.
Additionally, for SPF to work, organizations must keep their SPF records constantly updated – a time-consuming and cumbersome task that gets harder as companies change ISP providers.
DMARC vs SPF
DMARC, or domain-based message authentication, improves the sender policy framework protocol and the DKIM protocol. It prevents spoofing more successfully by requiring that the information in the "from" address align with other information about the sender. DMARC also requires that a message be authenticated with either SPF, DKIM, or both. It also improves reporting and details how messages that fail authentication should be handled.
FAQs
What is SPF and how does it relate to healthcare security?
Sender policy framework (SPF) is an email authentication protocol that allows domain owners to specify which mail servers are authorized to send emails on behalf of their domain. In healthcare, SPF helps prevent email spoofing, reducing the risk of phishing attacks that could compromise protected health information (PHI) and other sensitive data.
Why is SPF beneficial for HIPAA compliance?
SPF benefits HIPAA compliance because it helps ensure the authenticity of email communications, thereby protecting sensitive information from phishing and spoofing attacks. By implementing SPF, healthcare organizations can prevent unauthorized parties from sending fraudulent emails using their domain, thereby safeguarding PHI and maintaining compliance with HIPAA’s security requirements.
What are the potential risks associated with not using SPF under HIPAA?
- Email spoofing: Increased likelihood of attackers sending emails that appear to come from a trusted healthcare domain, leading to phishing attacks.
- Data breaches: Compromise of sensitive patient information through deceptive emails that trick recipients into divulging PHI.
- Financial fraud: Potential for attackers to use spoofed emails to conduct financial scams or unauthorized transactions.
- Loss of trust: Damage to the organization's reputation and patient trust due to association with phishing or spoofing incidents.
- Non-compliance: Failure to implement technical safeguards as required by HIPAA, leading to potential fines and legal consequences.
See also: HIPAA Compliant Email: The Definitive Guide
