3 min read

This is the script I used when presenting "Why Email Needs a Zero Trust Security Model" during the HITRUST Collaborate 2021 online conference on 5 October 2021.
Introduction
Aloha! Welcome to HITRUST Collaborate 2021. My name is Hoala Greevy, I’m the Founder CEO of Paubox, and we are grateful to be a Platinum sponsor for this year’s online event.
As the HITRUST website states, if safeguarding sensitive information is important to your organization, your company will want to be a part of this high-impact event.
At Paubox, our mission is to become the market leader for HIPAA compliant email in the United States. Inherent in our mission is data security and the safeguarding of information; specifically email, as it enters and leaves your organization’s inboxes.
Furthermore, the goal of HITRUST Collaborate is to enable attendees to learn, collaborate, and ultimately deliver more effective methods for risk management, compliance, and information protection.
We’re here to say this presentation is directly aligned with these goals, as you’re going to learn about Zero Trust Email, a patent-pending solution we built this year, to address the latest phishing and ransomware tactics being employed by bad actors.
You’ll also learn how Zero Trust Email and Paubox can help with your risk management and compliance goals.
About Paubox
Before diving in, here’s a quick blurb to get on the same page about what we do, what’s important to us, and how we do it:
Paubox is for healthcare organizations seeking to remove friction from their HIPAA Compliant Email communications.
Paubox is a cloud-based, B2B SaaS solution that provides a seamless user experience for both senders and recipients of secure, compliant email.
Unlike incumbent solutions that force recipients to login to a portal to read a secure message, Paubox allows the recipient to read a secure, compliant email in their inbox, just like a normal message.
In our business, we know customers want security, reliability, and ease of use. Trends that don’t change are big ideas. And these big ideas are worth paying attention to, even if they appear banal.
For example, there’s precisely a 0% chance a customer ten years from now will come to us and say, “I really love Paubox, but could you make it a little less secure?”
The same goes for a customer telling us, “Big fan of Paubox, but could you throw in more downtime?” or “Hey, can you make Paubox harder to use? Can you make it harder for us to get in touch with tech support?”
In effect, we can build sound business strategies around big ideas that remain stable over time.
We also know that customer feedback is a Paubox Foundation- a principle we care deeply about. The open secret here at Paubox is that we use customer feedback as our roadmap of what to build and when.
In fact, it was precisely customer feedback given to us in 2018 that embarked the journey that is known as HITRUST CSF certification.
As context, three years after our launch in 2015, it became clear that if we wanted to break into the enterprise and even mid-market healthcare segments, we would need to attain some type of third party certification.
HITRUST and SOC 2 were being mentioned by our customers and it was initially hard to tell which one to pursue. But after tallying responses, it was clear our customers were asking for, if not requiring, HITRUST CSF certification a lot more than they were for SOC 2. Thus began our foray into HITRUST in 2018.
After linking up with Michael Parisi of HITRUST later that year, our certification journey accelerated. In February 2019, we completed the HITRUST RightStart program, which aims to give startups the tools needed to make information security and compliance easier to establish and manage. We were the first company to complete RightStart and we happily participated in a case study with HITRUST. I also believe we are the first email encryption company to achieve HITRUST CSF certification.
Fast forward to this April, we also joined the HITRUST Shared Responsibility and Inheritance Program.
This program enables participating service providers that have previously completed the HITRUST CSF Certification process to allow their customers undergoing a HITRUST CSF Assessment to inherit one or more controls from their provider’s assessment, thus saving customers time and money.
In other words, you can leverage this program to accelerate your organization’s risk management and compliance objectives.
The HITRUST Shared Responsibility and Inheritance Program can be applied to any of our three HITRUST CSF certified solutions:
So in a nutshell, we can already see that:
- Security is a big idea here at Paubox and the HITRUST CSF certification is the gold standard representation of our commitment to it.
- We used customer feedback as guidance on what certification to pursue. HITRUST CSF was the obvious choice.
- Ease of use is another big idea at Paubox. We believe the HITRUST Shared Responsibility and Inheritance Program makes it even easier for organizations to partner with participating service providers like us to complete their HITRUST journey.
Security. Customer feedback. Ease of use. In the following slides, you’ll see how we used those same big ideas and concepts to build Zero Trust Email.
Next slide, please.

Tenet: We are in a Quiet War
A tenet, or a foundational element behind today’s presentation, is that we are in the midst of a quiet war with several hostile nations.
In 2021, the best way to conduct a quiet war is online.
For starters, it’s cheaper to hire or associate with a group of blackhat hackers than it is to buy a tank, a submarine, or an aircraft carrier. It’s also easier to deny knowledge of or responsibility for their actions. This is known as plausible deniability.
In both cases, China and Russia excel at this.
Online Threats Aren’t Going Anywhere
We have ample data to support our tenet. First of all, online threats aren’t going anywhere.
Research shows that 93% of healthcare organizations have reported at least one security breach in the past three years. Earlier this summer, ransomware attacks were striking an organization every 8 minutes in the U.S.
And as we’ll see in a few minutes, bad actors are now successfully bypassing industry standard email security checks like DKIM, SPF, DMARC, and RBL.
Next slide, please.
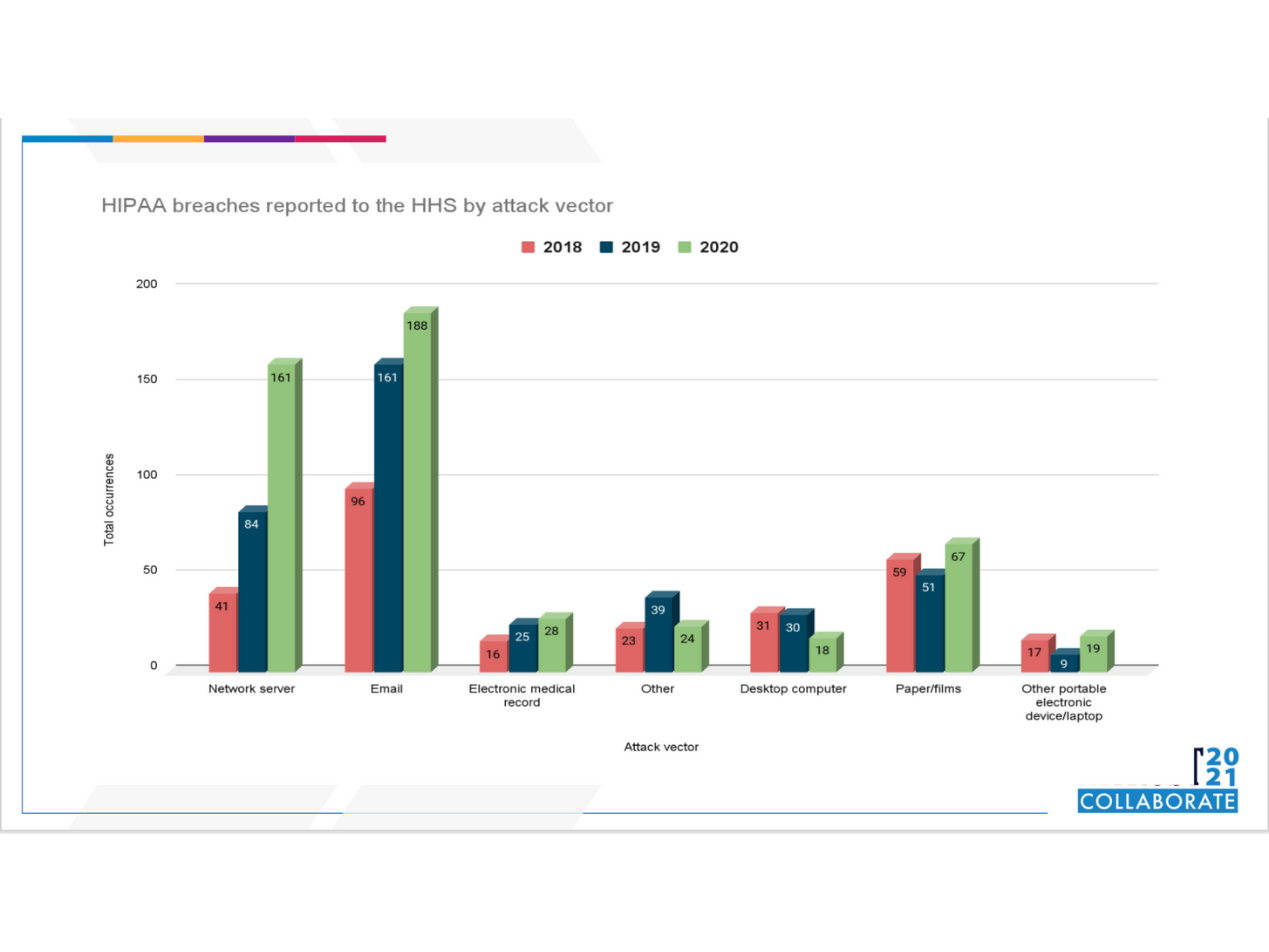
HIPAA Breaches
If we take a look at data going back to 2018, we can easily spot a trend when it comes to successful online attacks in U.S. healthcare. It’s more than likely to occur via email or by compromised servers.
As context, here’s how we compiled the data on this slide.
Under the 2009 HIPAA Breach Notification Rule, it became mandatory for healthcare providers (and their business associates) to report all data breaches of unsecured protected health information (PHI). An organization must first notify the U.S. Department of Health and Human Services through its breach notification portal. This portal is also called the HHS Wall of Shame.
What’s odd about the HHS Wall of Shame is that it only retains data for two years. Being a government site, it’s also quite hard to glean trends from.
Starting in July 2017, we began the Paubox HIPAA Breach Report. Our monthly report analyzes data sent to the HHS Wall of Shame and makes it easy to use and understand. Now that we’ve been doing it for over four years, we have a unique collection of data that’s available nowhere else. Don’t forget, the Wall of Shame only retains data for two years.
And for each year we’ve been covering it, one trend has remained constant:
Email is the most likely vector in which a healthcare organization will get breached.
As for 2021, we need only to recall Microsoft’s notice in March about tens of thousands, or maybe even hundreds of thousands, Exchange servers in the U.S. being hacked by Chinese bad actors.
Can anyone remember what that attack was called? There’s been so many this year alone, it’s hard to remember isn’t it? Here’s the answer: it was called Hafnium and it employed four consecutive zero-day exploits in its attack chain.
Next slide, please.

Email Threats Evolving
As the aforementioned Hafnium attack illustrated, email threats are evolving. As context, up until then, the world had not seen a string of four consecutive zero-day exploits in a single email, or in this case, email server attack.
Even having access to a single zero-day exploit can be very expensive to develop or attain. Having four at disposal and stringing them together? It’s clearly a sign of a bad actor, in this case a nation state, with access to a vast array of resources and a focus on causing chaos in the United States.
But that’s not the only way in which email threats evolved in 2021.
Earlier this year, our customers began reporting to us an increase in phishing attacks that got past the email security service that’s available with Paubox Email Suite. Knowing that security and customer feedback are obsessively important at Paubox, we asked our customers to forward us some examples.
Upon closer inspection, we noticed these new phishing campaigns had one thing in common:
The bad actors used American tech companies to send the malicious email.
And if they’re using American tech companies like AWS, Mailgun, Sendgrid, and IBM to send phishing campaigns, then of course they will bypass all known industry standard email security checks like DKIM, SPF, DMARC, and RBL. These American companies make it their business to have their email systems in compliance with industry standards.
What's new however, is the bad guys now have crossed the moat, opened the drawbridge, and are now in the castle.
Next slide, please.
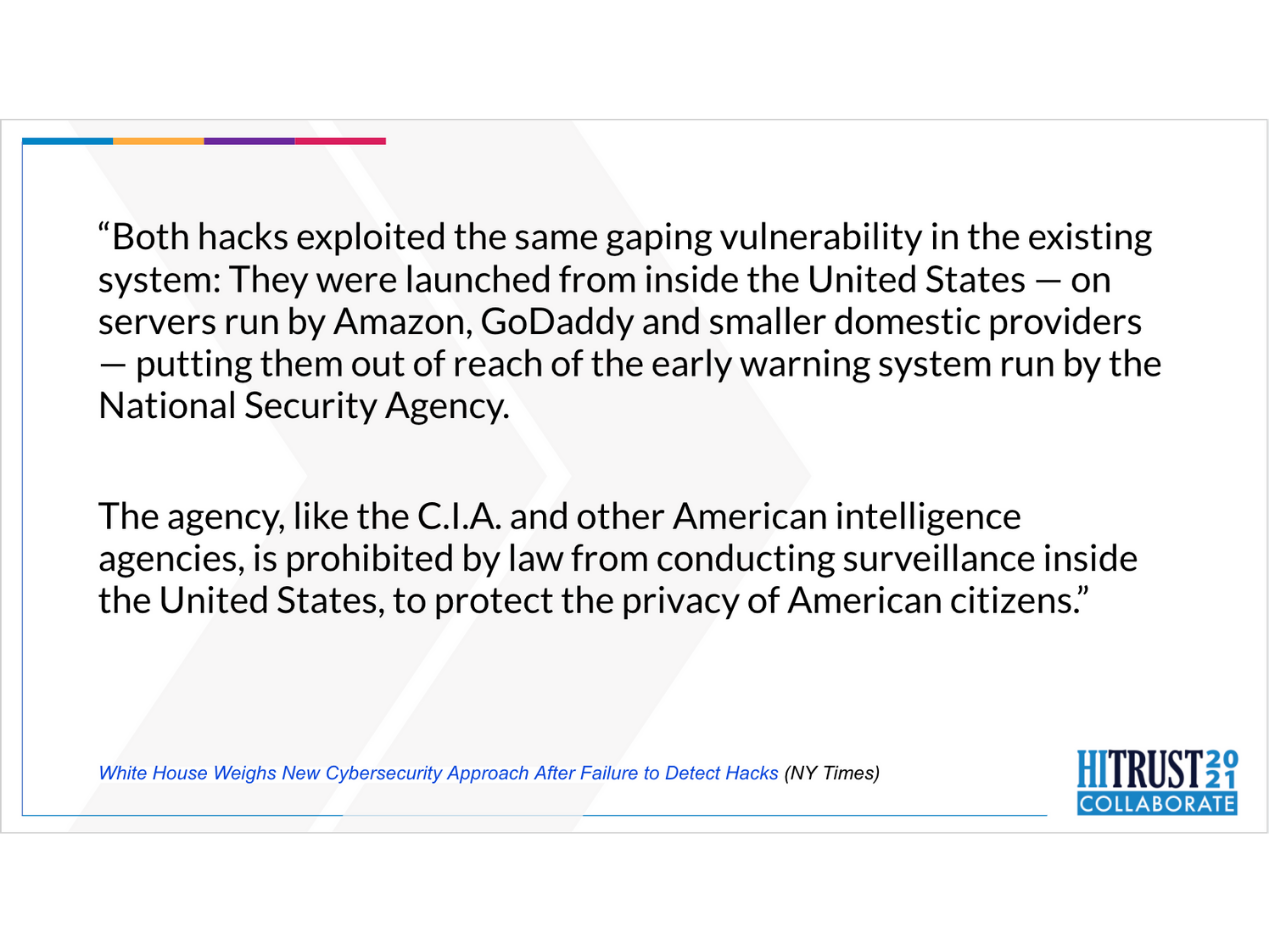
At the same time our customers were sending us these phishing examples, we also saw articles pointing to the fact that bad actors have identified America’s blind spot: If hackers can assemble an attack from inside America’s borders, the U.S. government can be blindsided.
Here’s a quote from a New York Times article in March:
“Both hacks exploited the same gaping vulnerability in the existing system: They were launched from inside the United States — on servers run by Amazon, GoDaddy and smaller domestic providers — putting them out of reach of the early warning system run by the National Security Agency.
The agency, like the C.I.A. and other American intelligence agencies, is prohibited by law from conducting surveillance inside the United States, to protect the privacy of American citizens.”
This was the “Aha! moment” for us at Paubox:
We can no longer trust email sent from American hosting and infrastructure companies.
It was then in March we decided a new system must be devised. And quickly.
Next slide, please.

Ransomware in the News
Over the summer, we also witnessed an explosion in ransomware attacks. Colonial Pipeline, JBS, and Scripps Health faced multi-million dollar losses via ransomware. In the case of Scripps, they announced they expected to lose nearly $107 million from their ransomware attack.
In fact, President Biden recently became the first American president to say the word ‘ransomware’ in public. That same week in May, he issued an Executive Order on Cybersecurity.
As we can clearly see, the United States urgently needs private sector innovation to keep ransomware and phishing attacks at bay.
We were already hard at work on a solution.
Next slide, please.
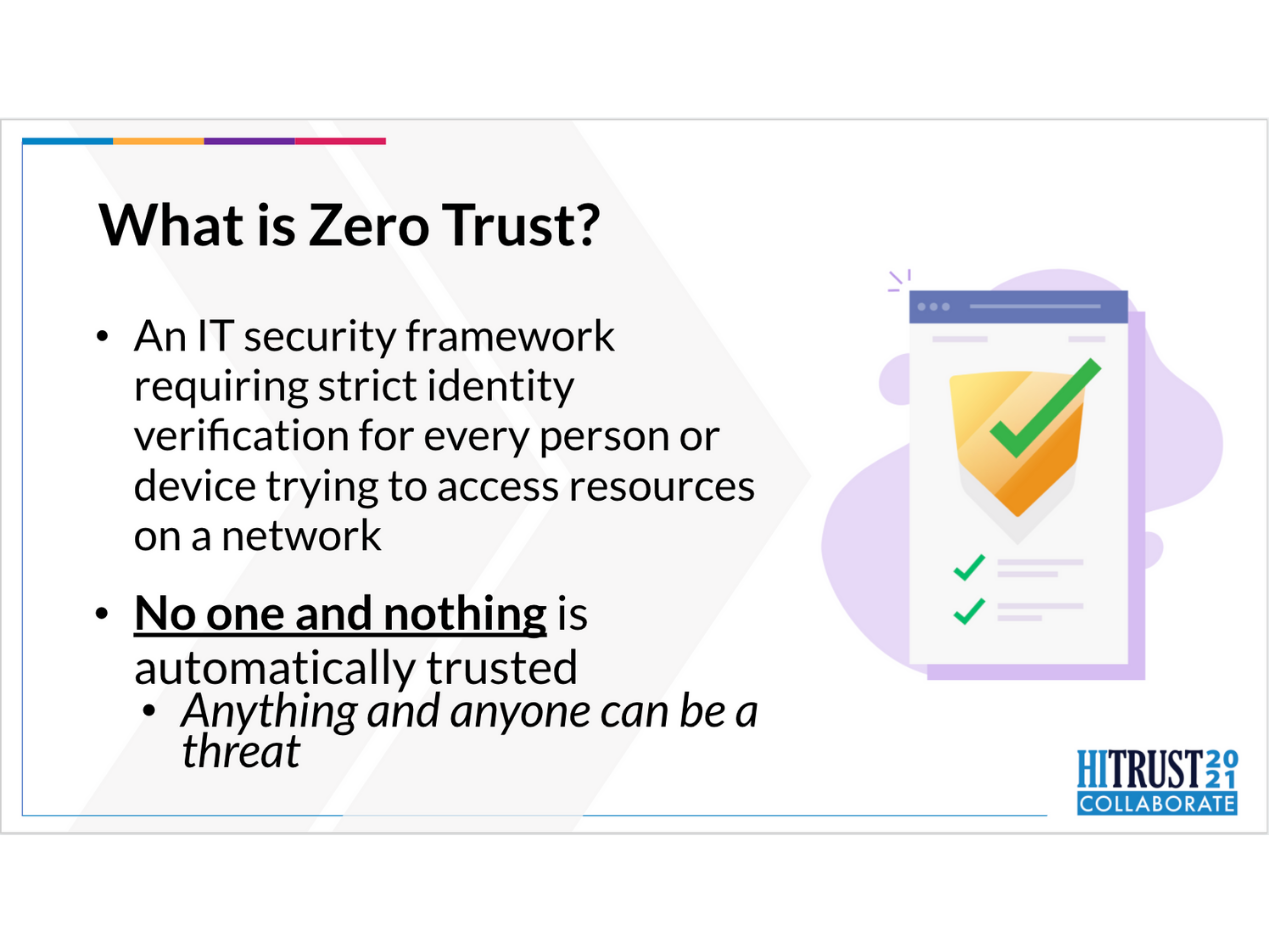
What is Zero Trust?
As we reflected on what customer feedback showed us, coupled with breaking news, it was clear to us the metaphor of the bad guys already being inside the castle was indeed correct.
Then as we began to devise a new and novel method by which to address this, the Zero Trust Security model became an apt starting point.
As the slide shows, the Zero Trust security model is an I.T. security framework requiring strict identity verification for every person or device trying to access resources on a network. No one and nothing is automatically trusted; anything and anyone can be a threat.
Next slide, please.
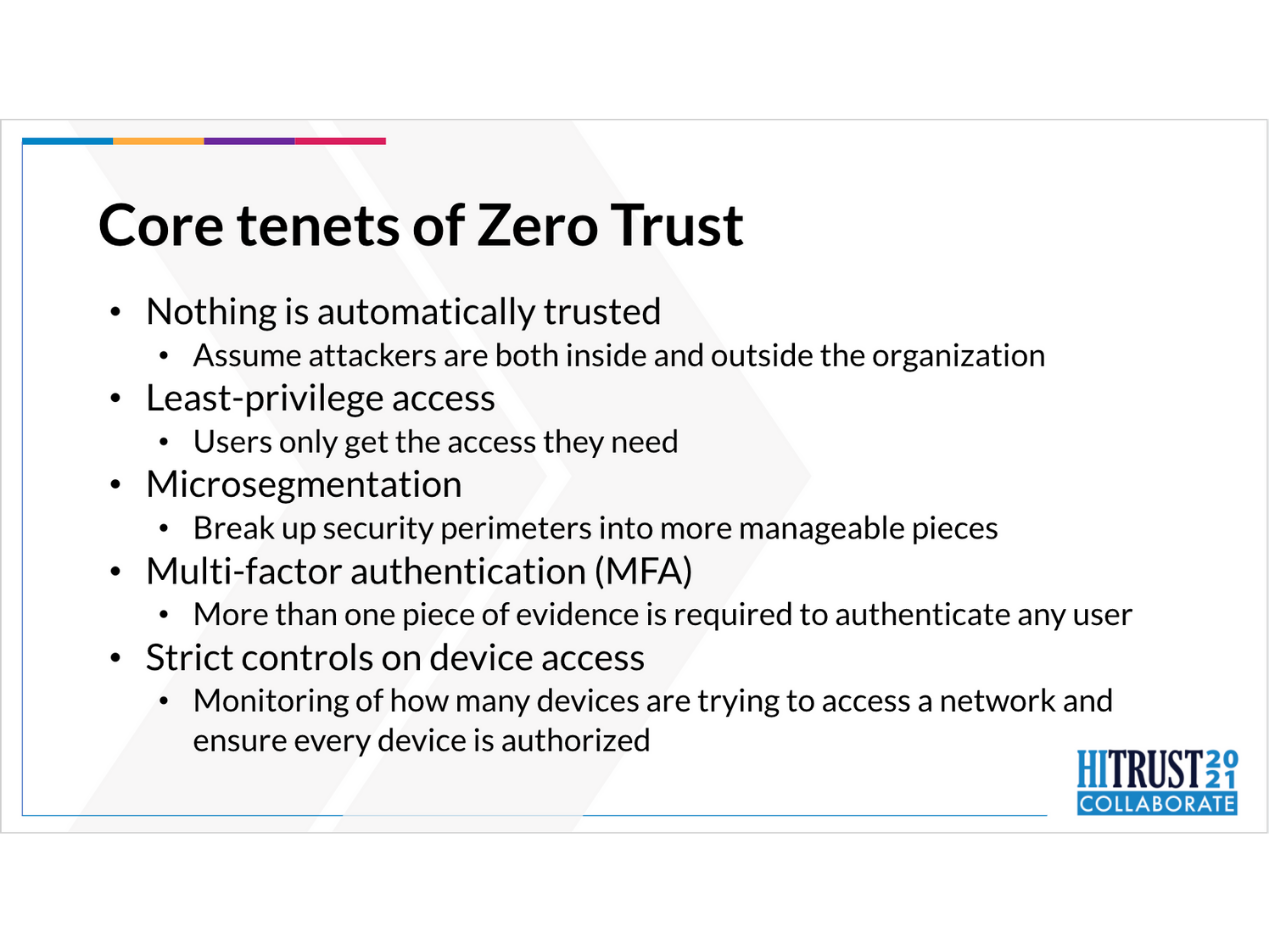
Core Tenets of Zero Trust
The guiding principles behind zero trust security are:
- Nothing is automatically trusted
- Least-privilege access
- Microsegmentation
- Multi-factor authentication (MFA). A core value of zero trust security, MFA simply means more than one piece of evidence is required to authenticate a user.
- Strict controls on device access
For the purposes of what we ended up building, which we’ve coined as Zero Trust Email, let’s focus on MFA.
In our case, we realized what we needed to build was a new, additional piece of evidence to prove an incoming email really was who it claimed to be.
It had to be a new set of data because existing authentication mechanisms like DKIM, SPF, RBL, etc. were of no meaningful use to us if the attacks were originating from these legitimate, American infrastructure companies.
In a nutshell, we had to devise a new piece of authentication between a sending mail server with the Paubox cluster of inbound email security instances.
Next slide, please.

How Zero Trust Email can help
What we built with Zero Trust Email is a new and novel MFA algorithm that:
- Depending on content and context, requires an additional piece of evidence from a sender’s mail server before delivering a message to its recipient.
- The additional MFA evidence is unique for each customer and changes based on time and usage.
As a hypothetical example, let’s say a bad actor executes the following phishing campaign:
- Three years prior, register a domain called officeinvoicez.com and keep its reputation clean or at least neutral. In other words, the domain is not listed on any RBL sites like Spamhaus.
- Sign up for an account on Amazon Web Services using an American bank account and set up proper DKIM, SPF, and DMARC records.
- Configure Amazon SES to send a phishing campaign to dozens of users within an organization around a fake renewal invoice for Microsoft Office.
- Launch the phishing campaign and target around 30% of the organization to get the same campaign within a 30 minute window.
If this sounds like too much work for anyone to do, especially step one where you hold a domain name for three years before launching an attack, it’s happening thousands of times, every day, to targets specifically within the U.S. And as the data and trends in this presentation have already shown, it works.
In this hypothetical example however, Paubox Zero Trust Email would catch and quarantine such an attack. Even if the domain is then changed to a slightly different yet neutral domain, even if the attack is then moved to GoDaddy or any other American infrastructure company.
Paubox Zero Trust Email was added to Paubox Email Suite in May. It’s patent-pending and available to customers at no additional charge. It’s also part of the HITRUST Shared Responsibility and Inheritance Program.
We used customer feedback to learn something needed to be done and we ultimately used customer feedback as the foundation of how to build it.
We believe that security, reliability, and ease of use are big ideas at Paubox. Each of which are universally worth expending time, resources, and capital to.
Thank you for your time today. I’ll now open the floor to questions.
Mahalo!

Subscribe to Paubox Weekly
Every Friday we'll bring you the most important news from Paubox. Our aim is to make you smarter, faster.



 Hoala Greevy
Hoala Greevy