
Last updated: 28 January 2026
As 2026 begins, major HIPAA updates from 2025 are still not finalized, but enforcement isn’t slowing down. HHS has yet to complete proposed changes to the HIPAA Privacy Rule and a separate effort to modernize the HIPAA Security Rule. In the meantime, the Office for Civil Rights is continuing to clamp down on how organizations handle patient access requests, respond to information blocking concerns, and protect electronic health information. Even as the rules are evolving, compliance expectations are being enforced now, particularly regarding email encryption.
There's a good reason for the security and compliance focus on email. 170 email-related HIPAA breaches occurred in 2025, impacting over 2.5 million people, a trend that's unlikely to slow down in 2026. Overall last year, 1 in 3 breaches that landed on the "Wall of Shame" had email as the attack vector with an average cost of $7.5 million in penalties and settlements.
This guide is for healthcare professionals, IT staff, and anyone responsible for maintaining or acquiring a HIPAA compliant email solution.
Table of contents
- HIPAA compliance and email security
- When does an email need to be HIPAA compliant?
- What's new in 2026?
- What makes email HIPAA compliant?
- What to look for in a HIPAA compliant email solution
- How to send HIPAA compliant emails
- HIPAA compliant email checklist
- HIPAA violations and fines
- Email encryption methods
- Frequently Asked Questions
HIPAA compliance and email security
The HHS says that HIPAA "allows covered health care providers to communicate electronically, such as through email, with their patients, provided they apply reasonable safeguards when doing so."
They clarify that "patients may initiate communications with a provider using email. If this situation occurs, the health care provider can assume (unless the patient has explicitly stated otherwise) that email communications are acceptable to the individual."
At the same time, The Security Rule's Technical Safeguards require "technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network."
So, to ensure HIPAA compliance when using email, you must use secure email solutions that encrypt messages and attachments in transit and at rest.
It's now common practice to use an email service provider like Google Workspace or Microsoft 365 to host your organization's email while using a separate HIPAA compliant email service to provide additional protection, such as email encryption, security, data loss prevention, and backups.
Go deeper: Why Google Workspace and Microsoft 365 aren't enough for complete HIPAA compliance
When does an email need to be HIPAA compliant?
Two types of entities must follow HIPAA regulations: covered entities and their business associates. If you're a healthcare provider, a health plan, or a healthcare clearinghouse, you're a covered entity. A business associate is someone who provides services to covered entities.
Any email sent by a covered entity or a vendor that contains PHI must be HIPAA compliant.
By the way, if you're not 100% certain whether HIPAA applies to you, follow this step-by-step guide.
Go deeper:
What's new in 2026?
Last year, we reported that the Office for Civil Rights released a Notice of Proposed Rulemaking titled HIPAA Security Rule To Strengthen the Cybersecurity of Electronic Protected Health Information. "This proposed rule to upgrade the HIPAA Security Rule addresses current and future cybersecurity threats," said then OCR Director Melanie Fontes Rainer. "It would require updates to existing cybersecurity safeguards to reflect advances in technology and cybersecurity, and help ensure that doctors, health plans, and others providing health care meet their obligations to protect the security of individuals' protected health information across the nation."
Proposed modifications to HIPAA's Security Rule included making "addressable" (i.e., flexible) standards under the Rule now "required." That means it's likely that all emails containing protected health information would be required to be encrypted.
Going into 2026, OCR’s major HIPAA Security Rule overhaul is still not final, but it is very much alive. The proposal was initially published in January 2025,and OCR has since been working through thousands of comments, and we're expecting to hear updates in May 2026.
In the meantime, regulators are pushing toward more explicit, measurable cybersecurity requirements, especially around protecting ePHI in transit, including email. So even before the rule is finalized, healthcare organizations should treat the proposal as a roadmap and tighten safeguards now.
What makes email HIPAA compliant?
Use a HIPAA compliant email service, like Paubox, that encrypts email messages and attachments in transit and at rest.
Always make sure you've signed a businss associate agreement (BAA) with the HIPAA compliant email service. Without that BAA, it's simply not HIPAA compliant.
A BAA is a contract between a HIPAA-covered entity and a vendor with access to PHI. It ensures that the email service will protect this information in compliance with HIPAA regulations.
There are a few other things to keep in mind. You can get our full HIPAA compliant email checklist below.
- Don't delete emails. It's recommended that electronic PHI be retained for at least six years.
- Have access controls. Access controls ensure the people who should have access to emails are the only ones with access.
- Set up secure communication policies and procedures. All employees must know their responsibilities regarding handling and transmitting PHI via email.
- Train your staff on secure, HIPAA compliant email best practices.

What kinds of emails need to be HIPAA compliant?
When daily emails number in the hundreds or even thousands, mistakes will always happen, so the safest way to avoid both stress and HIPAA violations is to encrypt everything automatically. A study titled Human Factors in Electronic Health Records Cybersecurity Breach found that "73.1 percent of all affected records resulted from breaches caused by unintentional factors" - human error - so relying on staff to avoid sensitive info in emails or knowing which emails must be encrypted is a high-risk approach.
Not every email includes PHI and may not technically need to be encrypted, but it's for that reason that encryption-by-default offers is the way to go for peace of mind.
What to look for in a HIPAA compliant email solution
Some encrypted email providers are difficult to set up and require special steps whenever sending an encrypted email. Go with the straightforward option every time. Use a HIPAA email provider that works with your existing email service and requires little to no training for your staff.
Also, make sure it's easy for your patients. Patients don't like logging in to portals to read emails.
Patients decline portal use because, as was shown in Acute Care Patient Portal Intervention: Portal Use and Patient Activation, "they were not interested (56.52%)", or "it involved too much technology (14.52%), having difficulties in using or accessing the portal. Even among those who opted to use the portal, 65% did not use the portal beyond the first day.
A similar study called Benefits, Problems, and Potential Improvements in a Nationwide Patient Portal found several issues with portals in healthcare communication:
- 21.9% of participants experienced "difficulty in navigating the service and searching for information" as the service was "badly organized and had problems switching between pages."
- 13.2% reported "delayed health data"
- 10% encountered "service problems" (such as the app not opening)
- 10% had issues with "patient portals getting mixed up"
- 8.7% faced "inconveniences in logging in"
That's why emails sent through Paubox are opened directly in the inbox, like every other email.
We looked at the prevalence of human error in HIPAA violations, and that's why default or blanket encryption is the smart choice for HIPAA compliance and email. When every email is assumed to include PHI, there's no risk of mistakes, so we recommend that every email sent by a covered entity be encrypted.
Go deeper: Why patient portals are inconvenient: An evidence-based perspective
HITRUST certification and HIPAA compliant email
There's no official HIPAA certification, so how can you trust a HIPAA email service provider? HITRUST.
Having HITRUST certification means that a company has taken extensive security measures to ensure the security of sensitive data. Working with HITRUST-certified vendors can lower insurance premiums and minimize legal liability.
We recommend any HIPAA compliant email solution you choose be HITRUST certified.
Osterman Research found that 80% of Organizations fell victim to an email security breach in the past 12 months and that 75% of Cybersecurity Threats arrive through email, and yet the recently published 2024 Trust Report shows that less than 1% of HITRUST-certifications experienced a breach over the past two years.
That's why Paubox is HITRUST certified.
Paubox CEO Hoala Greevy explained, "Since getting our first HITRUST certification in 2019, we have successfully renewed every year since, with no gaps in coverage."
How to evaluate a HIPAA compliant email provider
Before signing up with an HIPAA compliant email service, review the below points.
- HIPAA compliance: Is the company HIPAA compliant? Does the email service provider focus on healthcare specifically?
- Usability/integration: How easy is integrating the service into existing platforms? Is it easy for providers and administrators to use?
- Customer service: What avenues do customers have when they need help?
- Encryption system: Does the service encrypt emails or use portals? Does encryption need to be done manually, or is it automatic?
- Reviews: What are the reviews of the service? How is it rated?
- Breaches: Has the company ever experienced a data breach?
- Pricing structure: How does the company price its service? What is included in their plans?
We recommend Paubox for HIPAA compliant email, but here are questions to ask a possible HIPAA email service before making your decision.
- Is it easy to set up and easy to use for you and your staff?
- Can your recipients view the email in their inbox without portals or extra steps?
- Is email encrypted in transit?
- Is email encrypted at rest?
- Is every email encrypted by default?
- Will each vendor that processes or handles PHI in email sign a business associate agreement with your organization?
- As a best practice, is the HIPAA compliant email solution HITRUST certified?
What's next: Top 10 HIPAA compliant email services
How to send HIPAA compliant emails
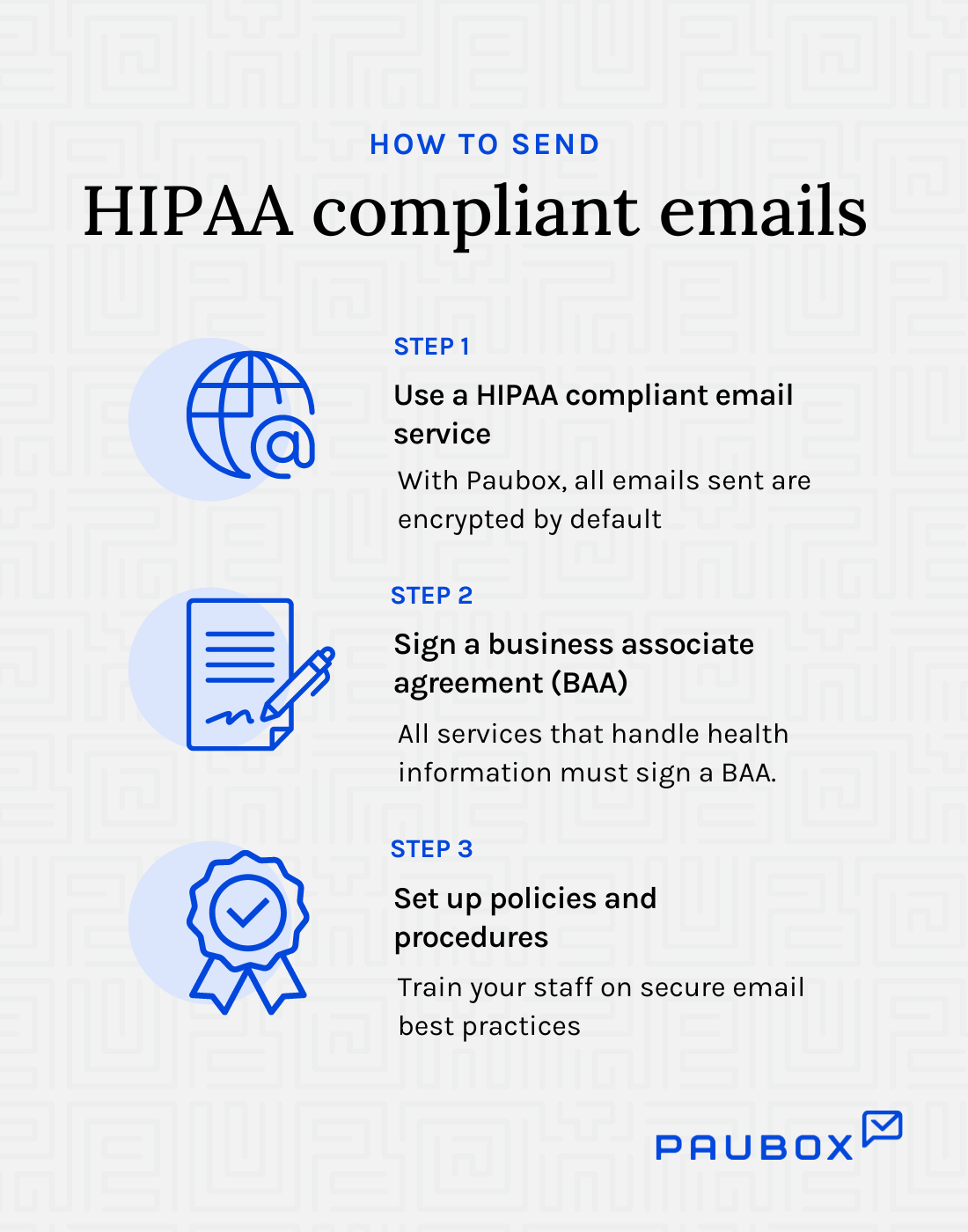
To start, you'll need a Google Workspace or Microsoft 365 account.
Next, sign a business associate agreement with Google or Microsoft to guarantee your emails will be encrypted at rest. However, it's not actually enough to ensure complete HIPAA compliance when sending emails - i.e., encrypted in transit.
Use a secure HIPAA compliant email service, like Paubox, that ensures every email encryption by default. Paubox offers seamless integration with existing email clients like Google and Microsoft to ensure 100% HIPAA compliance. You send the emails from your Google or Microsoft account. Paubox handles the encryption automatically, and your recipients open the email in their inbox. No portals or extra passwords needed.
This all takes about 15 minutes to set up once, and then every email is encrypted and HIPAA compliant by default.
HIPAA compliant email checklist
We've created a HIPAA compliant email checklist. The high-level steps are listed below, but there are a few more tasks to check off to be in compliance. These sub-tasks are listed in our free PDF download.
Get the HIPAA compliant email checklist
- Determine HIPAA applicability and scope
- Select an email service provider and sign a business associate agreement
- Develop access control policies and two factor authentication
- Establish email usage policies
- Document compliance measures
- Train staff regularly
- Conduct regular risk assessments
- Implement an incident response plan
- Review and Update Policies
- Additional document Compliance Measures
- Use a HIPAA compliant email provider that offers inbound email security
It's less complicated than it might appear at first, and using a HIPAA compliant email service will help you through steps like setting up DKIM and SPF records to ensure secure email delivery.
HIPAA violations and fines
Keeping your email communication HIPAA compliant is required by law, and penalties for HIPAA violations can be severe. Both civil and criminal penalties can be enforced by the U.S. Department of Health and Human Services (HHS) Office for Civil Rights.
In general, data breaches that fall under reasonable cause range from $100 to $50,000 per breach. Willful neglect cases range from $10,000 to $50,000 and often result in criminal charges being brought against the people involved.
This chart shows how civil penalties can reach a maximum of $1.5 million per violation:

Criminal penalties can also be applied when HIPAA violations are knowingly committed, with increases in the fine per violation and imprisonment.
Read more: The complete guide to HIPAA violations

Paubox HIPAA Breach Reports
The Paubox HIPAA Breach Report analyzes protected health information (PHI) data breaches affecting 500 or more people as reported to the Department of Health & Human Services (HHS).
Paubox has been compiling a monthly HIPAA Breach report since June 2017. Since then, the data clearly shows email breaches are statistically the most likely entry point for an organization to suffer a HIPAA breach.
Paubox's 2025 Healthcare Email Security Report highlights how email remains the leading attack vector, resulting in financial penalties, compromised patient data, and increased enforcement actions from regulators.
- 43.3% of data breaches involved Microsoft 365, possibly due to misconfigurations in email security settings.
- 264% increase in ransomware attacks on healthcare since 2018, with email as the primary attack method.
- Only 1.1% of analyzed healthcare organizations had a low-risk email security posture, highlighting systemic vulnerabilities.
- HIPAA fines exceeding $9 million were issued due to email security failures, including Solara Medical Supplies' $9.76 million settlement.
- $9.8 million was the average cost per healthcare email breach.

Access the full 2025 healthcare email security report for insights from 180 email-related healthcare breaches and actionable steps to protect your healthcare organization
Email encryption methods
There are five approaches to encrypting email for secure communication:
1. Transport Layer Security (TLS). This encryption protocol is used to secure the communication channel between email clients and email servers. When an email is sent over a modern TLS connection, the data is encrypted in transit, making it impossible for bad actors to decipher the content.
There are a few caveats with TLS when it comes to encrypting email:
- As of today, only TLS 1.2 and 1.3 are considered secure. TLS 1.0 and 1.1 are not secure.TLS 1.2 and 1.3 support stronger encryption algorithms and implement a more secure handshake process to better protect against known attacks.
- If the recipient mail server is not setup to accept to TLS email via STARTTLS, the email is automatically downgraded to clear text and is sent unencrypted over the internet. This is because the email protocol (SMTP) was designed with message delivery as its highest priority. Message encryption is a lower priority with SMTP. Our deep domain and technical expertise in email security resulted in our first patent directly addressing this issue.
TLS offers advantages over PGP and S/MIME in real-time communications by supporting more modern encryption algorithms, providing perfect forward secrecy, and enabling a more efficient secure connection establishment.
2. Pretty Good Privacy (PGP). This method uses public key cryptography to encrypt email messages and attachments. The sender uses the recipient's public key to encrypt the email, and the recipient uses their private key to decrypt it.
However, there are considerable caveats to using PGP for email encryption:
- Security. PGP has been criticized for having numerous security vulnerabilities in the past. We cannot find proof that EFAIL, a PGP vulnerability discovered in 2018, has ever been effectively patched.
- Complexity. PGP requires users to generate and manage their own public and private keys. In addition, each recipient's public key needs to be installed on every device used to check email.
- Lack of Integration. To work with most email clients, PGP requires additional software and plugins.
- Ease of use. PGP is less user-friendly than other encryption methods, making it far less adopted.
Go deeper: What does seamless encryption mean? Hint: It's not PGP
3. Secure/Multipurpose Internet Mail Extensions (S/MIME). S/MIME is a standard for public key encryption and signing of MIME data, which includes email attachments.
S/MIME requires both the sender and the recipient to have a digital certificate, which is used to encrypt and sign the message. The problem with S/MIME encryption is the same with PGP, it can longer support the claim it's secure.
As with PGP, S/MIME has legitimate caveats when it comes to encrypting email:
- Security. S/MIME also shares criticisms for having its share of security vulnerabilities. EFAIL also affects S/MIME.
- Complexity and ease of use. As with PGP, S/MIME is difficult to set up and use for providers and third-party users.
Go deeper: What is S/MIME and why isn't it the best form of email encryption?
4. Portals. About 15 years ago, when email security vendors noticed that PGP and S/MIME were not broadly adopted, email portals were popularized. If you've ever been forced to use one, you'll know it was not designed with user experience in mind.
The problems with this approach are apparent:
- Friction. The portal-based approach used by Microsoft 365 involves seven steps. Proofpoint's encrypted email solution has six steps. That's a lot of friction just to read a single secure email.
- User experience. Most email is now read from smartphones. Being forced to use a multi-step portal from a smartphone is widely agreed to be a terrible user experience.
- Backups and eDiscovery. As we can see in the case of the Iowa Department of Human Services, 432,000 emails were lost when switching away from a portal and app-based vendor (Virtru). This is because the emails were stored in their portal and not in the mailboxes of the Iowa DHS staff. When it came time for their staff to respond to eDiscovery requests, they ironically discovered they could not, as the encrypted email was unavailable. The sensitive data was stashed away in an unreadable format in a remote location.
5. Apps. About 10 years ago, when email security vendors took note of the low adoption of email portals, the leading thought was to build a smartphone app to handle email encryption.
Unfortunately, the same problems introduced by portals carried over:
- Friction. To read an encrypted email from an app, you need to download the app, register for an account, and learn how to use it. Since there isn't a de facto app for secure email, this means installing half a dozen or more apps. The logical thought process is, why? It's easy to see why this approach has too much friction.
- User experience. If most emails are now read from smartphones, that doesn't mean all are. The other use case (desktops) have been left out by optimizing for one use case by building an app. In some industries like healthcare, most staff use desktops for email. How exactly are you supposed to read an encrypted email sent from an app on an email client on your desktop? The answer is a portal - not a great user experience here either.
- Backups and eDiscovery. The problem with access to email archives and data is the same here as it is with portals. It's a glaring problem. For example, Virtru also has an app. This did not, however, prevent Iowa DHS from running into legal jeopardy (not to mention bad press) for their missing emails.
Frequently Asked Questions
Here are some frequently asked questions about HIPAA compliant email.
What is HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) is a federal law that was enacted in 1996. It sets national standards for protecting the privacy and security of certain health information, known as protected health information (PHI).
HIPAA includes two main rules: the Privacy Rule and the Security Rule. The Privacy Rule establishes national standards for protecting the privacy of PHI. It specifies how PHI can be used and disclosed and gives individuals certain rights with respect to their PHI.
The Security Rule establishes national standards for protecting the security of electronic PHI. It specifies administrative, physical, and technical safeguards that covered entities must implement to secure ePHI.
What is protected health information (PHI)?
PHI isn't just confined to medical records and test results. Any information that can identify a patient and is used or disclosed during the course of care is considered PHI, even if the information by itself doesn't reveal a patient's medical history.
Go deeper:
Who does HIPAA apply to?
HIPAA applies to covered entities, which include healthcare professionals, healthcare providers, health plans, and healthcare clearinghouses. It also applies to business associates of these covered entities. These are entities that perform certain functions or activities on behalf of the covered entity.
What is a business associate agreement?
A business associate agreement (BAA) is a written contract between a covered entity and a service provider. It is required by law for HIPAA compliance.
When working with a HIPAA compliant email service or any 3rd-party software that might handle PHI, HIPAA requires a business associate agreement outlining the responsibilities, obligations, and scope in complying with HIPAA's regulations.
At a minimum, a BAA must include ten provisions.
Is patient authorization needed to send PHI in email?
No. HIPAA's Privacy Rule allows healthcare providers to communicate with patients regarding their health and treatment as part of the healthcare provider's standard business practices. This can include sending emails containing PHI, provided that reasonable safeguards are in place to protect the information.
Providers still often obtain consent or acknowledge patient preferences about receiving communications via email at the start of their relationship, usually alongside a Notice of Privacy Practices.
Patients are informed about the risks associated with email communication and consent to receive health information through this medium.
For communication outside of standard treatment, payment, or healthcare operations like psychotherapy notes or marketing communications, explicit patient authorization is required under HIPAA before sending such information via email.
When does my HIPAA liability end when sending an email?
Once an email has been delivered to the end recipient's system using encryption, the covered entity or business associate has fulfilled their obligations to the HIPAA Privacy Rule.
Read more: How do I know when my HIPAA privacy obligation for email encryption ends?
Does a disclaimer make an email HIPAA compliant?
No. Emails must be sent securely to be HIPAA compliant. Adding a disclaimer does not meet HIPAA Security Rule requirements and doesn't make an email HIPAA compliant.
Is Gmail HIPAA compliant?
The free version of Gmail is not HIPAA compliant. Google will not sign a business associate agreement with free Gmail users.
For HIPAA compliant email, upgrade to a paid Google Workspace account and sign a business associate agreement. Even then, Gmail isn't 100% HIPAA compliant when sending emails to recipients that don't support TLS encryption. For emails to be 100% HIPAA compliant and avoid HIPAA violations, use Paubox Email Suite with Google Workspace to encrypt all emails by default.
Is Microsoft 365 HIPAA compliant?
Mostly yes. According to Microsoft, their encrypted emails work with other Microsoft email clients, but "if the recipient is using another email client or email account, such as Gmail or Yahoo, they'll see a link that lets them either sign in to read the email message or request a one-time passcode to view the message in a web browser."
Portals severely disrupt patient communication because accessing an email or attachment requires up to 6 extra steps. Use Paubox Email Suite with your Microsoft 365 account to encrypt all emails by default without needing patients to log in to a portal.
What should you do if you violate HIPAA in an email?
First, determine if the violation resulted in unauthorized disclosure of protected health information. If it did, notify the affected client promptly and take steps to mitigate any potential harm. Reporting the violation to the U.S. Department of Health and Human Services is required if the breach affects 500 or more individuals. Still, it's good practice to document all breaches, regardless of size.
Does the subject line of an email have to be encrypted?
If the subject line contains ePHI, it must be encrypted.
Does the email message header have to be encrypted?
There are many ways that PHI can be included in a message header. You should encrypt email message headers.
Do all email encryption methods encrypt a message header?
Email sent via Transport Layer Security (TLS) does encrypt the message header while it's in transit across the internet.
Email sent using PGP and S/MIME however, do not encrypt the message header.
Are email attachments encrypted?
Yes. Email attachments encrypted by either TLS, PGP, or S/MIME will be encrypted in transit.
Read more: What types of encryption methods encrypt email attachments?
Am I responsible for incoming emails to be HIPAA compliant?
HIPAA does not require covered entities and business associates to encrypt their inbound email.
If I password-protect an email attachment, does that make it HIPAA compliant?
The guidance from HHS is clear: forgoing encryption and only using password protection for a document (or an entire hard drive, for that matter) is not sufficient.
Read more: Is my password-protected PDF document HIPAA compliant?
What versions of Transport Layer Security encryption are considered secure?
In January 2021, the NSA issued the following guidance:
"The National Security Agency (NSA) emphatically recommends replacing obsolete protocol configurations with ones that utilize strong encryption and authentication to protect all sensitive information… Network connections employing obsolete protocols are at an elevated risk of exploitation by adversaries."
Furthermore:
"NSA recommends that only TLS 1.2 or TLS 1.3 be used; and that SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1 not be used."
Following NSA guidance, here's a list of security protocols supported by Paubox:
- SSL v2 (Not Supported)
- SSL v3 (Not Supported)
- TLS 1.0 (Not Supported)
- TLS 1.1 (Not Supported)
- TLS 1.2 (Supported)
- TLS 1.3 (Supported)
Read more: Paubox eliminates obsolete TLS protocols, follows NSA guidance
Do international companies need to abide by HIPAA?
If an international company handles or transmits PHI of U.S. citizens, it is subject to HIPAA regulations.
Read more: Do international companies have to abide by HIPAA?
Can a covered entity or business associate use a consumer email service provider like Yahoo or Hotmail?
We have not found a single consumer email service provider that provides a business associate agreement. Therefore, using a provider like Yahoo or Hotmail is not HIPAA compliant and should be avoided. Use a HIPAA compliant email service to secure your email.
Read more:
What is HITRUST?
HITRUST is a standards development organization founded in 2007 to unify security controls from federal law (HIPAA), state law, and non-governmental frameworks (PCI-DSS) into a single framework tailored towards use in the healthcare industry.
Paubox solutions have been HITRUST certified since 2019.
Does Paubox have patents for its work on encrypted email?
Yes, Paubox currently has four patents.
Read more: U.S. Patent Office approves our approach to email encryption
Is email marketing HIPAA compliant?
Yes, but very few email marketing platforms offer HIPAA compliant email marketing. Email marketing must meet two requirements to be compliant.
First, you must get authorization from patients to send them marketing emails. Second, the marketing emails must be encrypted. So, you'll need to use a HIPAA compliant platform, like Paubox Marketing.
Subscribe to Paubox Weekly
Every Friday we bring you the most important news from Paubox. Our aim is to make you smarter, faster.

 Hoala Greevy
Hoala Greevy



