According to research conducted by Sebastian Schinzel, a professor of computer security at Münster University of Applied Sciences, PGP and S/MIME have fatal security vulnerabilities. If these flaws are exploited, encrypted messages could decrypt into plain text communications, including encrypted emails sent in the past.
As a result, PGP and S/MIME are virtually ineffective in securing emails. If you or someone you know uses a secure email service that relies on PGP or S/MIME, beware: both encryption methods can fail and cost you a fortune in HIPAA violations. "There are currently no reliable fixes for the vulnerability. If you use PGP/GPG or S/MIME for very sensitive communication, you should disable it in your email client for now," Professor Schnizel warned.
Academics from KU Leuven University and Ruhr-University contributed to the PGP and S/MIME vulnerability research. The Electronic Frontier Foundation spoke with the European researchers and confirmed that "these vulnerabilities pose an immediate risk to those using these tools for email communication, including the potential exposure of the contents of past messages." Their advice?
Immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email.
The EFF has provided tutorials on how to disable PGP in Outlook, Thunderbird, and Apple Mail.

What is PGP and S/MIME's security vulnerability?
The name of the flaw in PGP and S/MIME has been aptly dubbed "Efail". Essentially, "if an attacker can intercept and alter an encrypted email — say, by sending you a new (altered) copy, or modifying a copy stored on your mail server — they can cause many GUI-based email clients to send the full plaintext of the email to an attacker controlled-server. Even worse, most of the basic problems that cause this flaw have been known for years, and yet remain in clients." The researchers estimate that some of these flaws have existed for more than a decade. The altered copy would be embedded into unviewable parts of an email and combined with HTML coding, making it virtually unnoticeable. According to the research group, the most serious vulnerabilities have resided in Thunderbird, macOS Mail, and Outlook for more than ten years. The flaws remain unfixed to this day. “If you use PGP or S/MIME for sensitive information then this is a big deal,” Matt Green, a professor specializing in encryption at Johns Hopkins University, told Ars. “It means that those emails are potentially not secure. There is a real attack that can be exploited by people that allows them to decrypt a lot of encrypted email.”
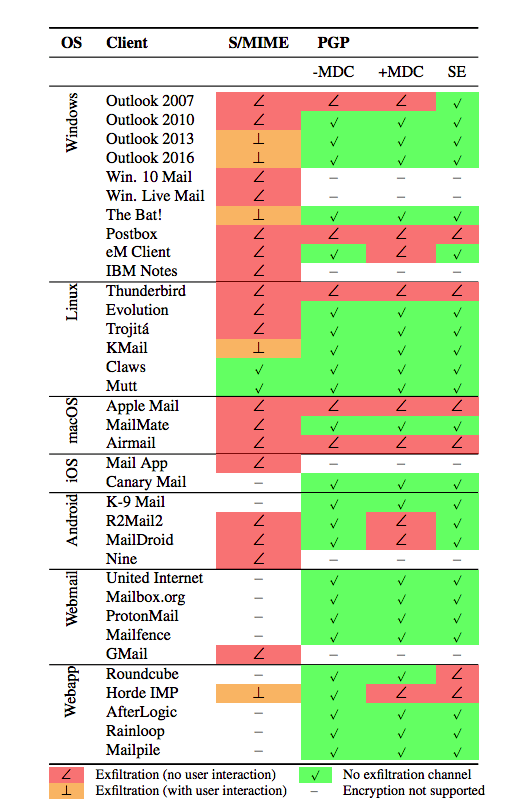
How Efail affects S/MIME and PGP clients
In the academics' research paper linked at the bottom of this article, the table below represents how Efail affects S/MIME and PGP respectively.
If you are a hardcore fan of PGP, I'm sorry to say that this is not the first time PGP has received negative press. It is not a personal favorite by those in the IT world.
READ MORE: What Does Seamless Encryption Mean? Hint: It's Not PGP
Large companies are placing the blame on email clients instead of taking any responsibility. However, Professor Matthew Green, a cryptography professor at John Hopkins University, argues against that blame: "PGP clients are vulnerable because 17 years after a vulnerability was known, the mitigation was not made a default in GnuPG and defense was instead 'left to PGP clients', which also make a convenient scapegoat when it goes pear-shaped." Filippo Valsorda, a cryptographer at Google, also added, "No, in 2018 you don’t get to claim the high ground and blame users and implementations if your crypto API returns the plaintext on a decryption error." The Efail flaw also lies in the CBC/CFB gadget attack issue.
As stated from the Efail website:
Professor Green also noted, "The real news here is probably about S/MIME, which is actually used in corporate e-mail settings. Attacking and modifying encrypted email stored on servers could actually happen, so this is a big deal."
RELATED: 3 Insider Threats You Need to Plan For
Read Professor Schnizel's full report about EFail, titled, Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels. You can also read FAQs about Efail on its dedicated website.
A seamless way to secure HIPAA compliant email
PGP and S/MIME are considered outdated forms of encryption by today's user-friendly standards. At Paubox, we call user-friendly email encryption - seamless encryption. In other words, it shouldn't take five clicks and a login to send or read a secure email.
WATCH: Dr. J. Gary Dela Cruz on Paubox: Seamless Encryption, No Passwords to Remember, Very Easy
Paubox makes HIPAA compliant email simple for you and your recipients. There are no portals, no plugins, and no extra steps. You deliver the patient care, we'll deliver your email securely. If you're ready to redefine your secure email experience, contact us today to get started.
Subscribe to Paubox Weekly
Every Friday we'll bring you the most important news from Paubox. Our aim is to make you smarter, faster.





